According to security firm BI.ZONE, the threat actor known as Paper Werewolf distributed the WinRAR exploits throughout July and August by sending booby-trapped archive files in emails that impersonated staff at the All-Russian Research Institute. The goal was to deploy malware that would give Paper Werewolf remote access to compromised systems.
Although ESET and BI.ZONE discovered the attacks independently, it remains unclear whether the threat groups exploiting the vulnerabilities are connected or simply obtained the same exploit from a shared source. BI.ZONE suggested that Paper Werewolf may have purchased the vulnerabilities from a dark-web crime forum.
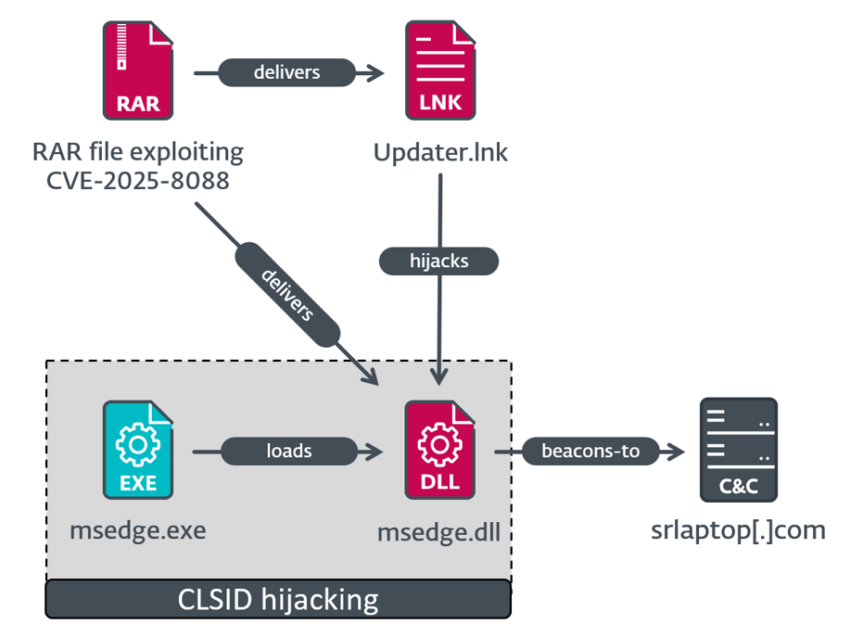
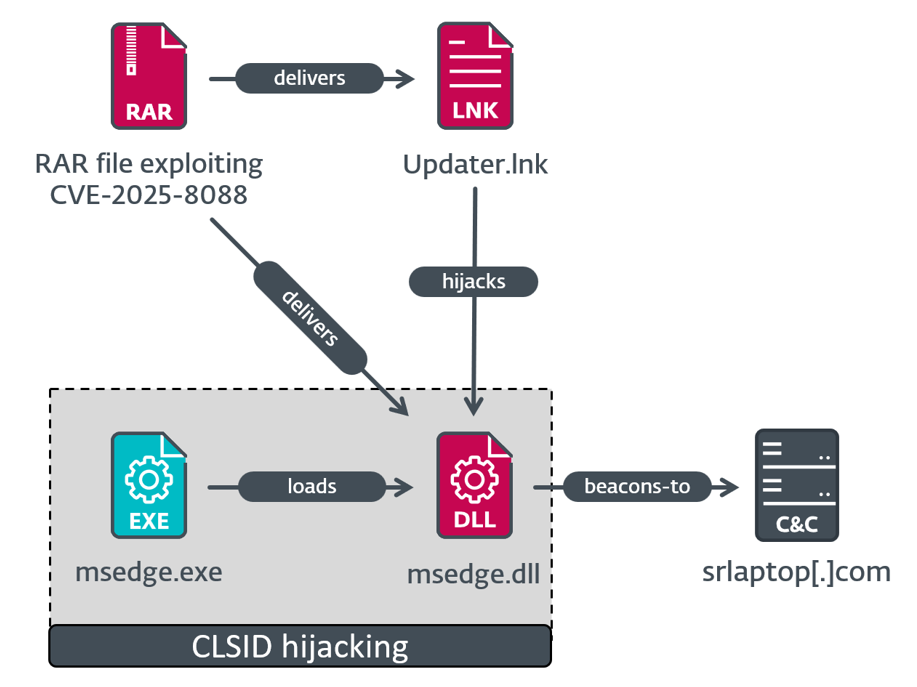
ESET reported that it observed three separate execution chains being used in the attacks. One chain—targeting a specific organization—leveraged a malicious DLL concealed inside an archive. The attackers used COM hijacking to ensure the DLL was executed by applications such as Microsoft Edge. The process unfolded as follows:
Illustration of the execution chain installing Mythic Agent.
Credit:
ESET
The DLL decrypted embedded shellcode that queried the machine’s domain name and checked it against a hardcoded target. If the values matched, the shellcode installed a customized version of the Mythic Agent exploitation framework.
A second execution chain deployed a malicious Windows executable that installed SnipBot, a known RomCom malware strain. This payload included sandbox-evasion logic and terminated immediately when executed inside empty VMs commonly used by researchers. The third chain relied on two additional pieces of RomCom malware: RustyClaw and Melting Claw.
WinRAR vulnerabilities have a long history of real-world exploitation. In 2019, a severe code-execution bug was widely abused by threat actors shortly after a patch was released. In 2023, another zero-day remained under active exploitation for more than four months before researchers detected it.
Part of the reason WinRAR is such an attractive target is its enormous global user base combined with the fact that the software does not auto-update. Users must manually download and install new versions—meaning many remain vulnerable for long periods. ESET also warned that Windows versions of UnRAR.dll and the portable UnRAR source code are vulnerable as well.
Security experts strongly advise avoiding all WinRAR builds prior to version 7.13, the most recent release at the time this article was published. While the update patches all known vulnerabilities, the steady stream of WinRAR zero-days suggests users should remain cautious.